The Importance Of Data Backups Protecting Your Information From Loss
페이지 정보

본문
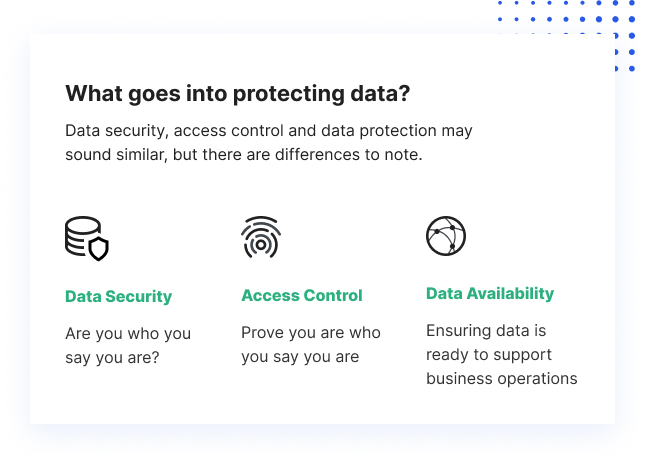
In the digital age, the preservation of electronic records is paramount. This section delves into the essential practices that ensure the integrity and availability of crucial digital content. By implementing robust strategies for regular archiving, individuals and organizations can mitigate the risks associated with unforeseen data erasure or corruption.
Why Regular Archiving Matters
Regular archiving serves as a critical defense mechanism against the myriad threats that can compromise digital assets. Whether it's accidental deletion, hardware failure, or malicious attacks, having a backup of your data can mean the difference between a minor inconvenience and a significant setback. This practice not only protects against data loss but also enhances overall operational resilience.
Enhancing Security Through Archiving
Archiving goes beyond mere data preservation; it plays a pivotal role in fortifying security measures. By maintaining copies of sensitive information in secure locations, organizations can ensure that even in the event of a breach, the impact is minimized. This proactive approach to data management is essential in today's landscape where cyber threats are increasingly sophisticated and prevalent.
The Critical Role of Data Backups
In this section, we delve into the pivotal strategy of averting the detrimental effects of digital asset disappearance. It is crucial to recognize the methods and importance of preserving crucial electronic records to ensure continuity and security in both professional and personal realms.
Preventing Data Loss: An Essential Strategy
Data preservation is not merely a reactive measure but a proactive approach to maintaining operational integrity. By implementing robust procedures for safeguarding digital content, entities can significantly reduce the risks associated with accidental deletion, hardware failure, or malicious attacks.
One of the primary steps in this strategy is the establishment of a comprehensive archiving system. This involves regular and systematic duplication of critical files, ensuring that even in the event of an unforeseen incident, the essential data can be recovered swiftly.
Moreover, it is vital to integrate advanced security protocols that protect these archives from unauthorized access and cyber threats. Encryption, opt out white pages multi-factor authentication, and secure access controls are integral components of a robust data preservation plan.
Education and awareness also play a critical role in this strategy. Regular training sessions for employees or individuals on best practices for data handling and security can significantly enhance the effectiveness of data preservation efforts.
In conclusion, the strategy of preventing data loss is multifaceted, encompassing technological solutions, security measures, and educational initiatives. By adopting a holistic approach, organizations and individuals can fortify their digital defenses and ensure the longevity and security of their valuable electronic assets.
Preventing Data Loss: An Essential Strategy
In this section, we delve into the critical measures necessary to ensure the security and integrity of sensitive digital assets. The focus is on strategies that prevent the irreversible disappearance of crucial files and records, which can have severe implications for both individuals and organizations.
Safeguarding digital assets is not merely about protecting against accidental deletion or hardware failure; it extends to defending against malicious attacks and breaches. Regular preservation of digital content is a fundamental step in mitigating risks associated with data corruption or theft.
| Strategy | Description | Benefits |
|---|---|---|
| Automated Scheduling | Setting up automatic routines to copy and store digital files at regular intervals. | Ensures consistency and reduces the likelihood of human error. |
| Off-site Storage | Storing copies of digital assets in a location separate from the primary site. | Protects against localized disasters such as fires or floods. |
| Encryption | Using algorithms to encode digital files, making them unreadable without the correct decryption key. | Enhances security against unauthorized access. |
| Regular Audits | Periodically reviewing and testing the effectiveness of preservation methods. | Helps identify and rectify potential vulnerabilities. |
Implementing these strategies not only helps in preventing the loss of digital assets but also ensures that privacy and security are maintained. It is crucial for entities to adapt and evolve their preservation practices in line with emerging threats and technological advancements.
Safeguarding Privacy Through Regular Backups
In this section, we delve into the critical measures necessary to preserve confidentiality and integrity in the digital realm. Regular maintenance of records is pivotal in thwarting potential breaches and ensuring that sensitive details remain secure. We will explore various threats that jeopardize the safety of these records and discuss effective strategies to counteract them.
Cyber threats are continually evolving, posing significant risks to the security of electronic records. Malicious actors employ sophisticated techniques to access or disrupt these records, which can lead to severe consequences for both businesses and individuals. Understanding these threats is the first step towards implementing robust protection measures.
| Threat Type | Description | Impact |
|---|---|---|
| Phishing Attacks | Deceptive attempts to obtain sensitive details by masquerading as a trustworthy entity in electronic communications. | Can lead to unauthorized access and data theft. |
| Malware Infections | Software designed to disrupt, damage, or gain unauthorized access to a computer system. | Can result in data corruption or loss. |
| Ransomware | A type of malware that encrypts files, demanding a ransom for their release. | Can paralyze operations and lead to significant financial losses. |
| Insider Threats | Security risks that come from within the organization, such as employees or contractors with access to sensitive information. | Can cause significant damage due to insider knowledge. |
To effectively safeguard against these threats, it is essential to implement a comprehensive strategy that includes regular updates of backup procedures. This not only ensures the availability of records in case of an incident but also enhances the overall resilience of the system against cyber attacks.
In conclusion, maintaining regular backups is a fundamental practice in the arsenal of cybersecurity measures. It is crucial for preserving the integrity and confidentiality of electronic records, thereby protecting against the myriad of threats present in the digital landscape.
Understanding Cybersecurity Threats to Your Data
In this section, we delve into the various digital perils that can compromise the integrity and availability of crucial files and systems. It is essential to recognize the spectrum of threats that exist in the digital realm, as awareness is the first step towards fortifying defenses against potential breaches.
Cyber threats are multifaceted, ranging from simple human errors to sophisticated malicious attacks. Below is a table outlining common types of cyber threats and their potential impacts:
| Type of Threat | Description | Potential Impact |
|---|---|---|
| Malware | Software designed to disrupt, damage, or gain unauthorized access to a computer system. | Data corruption, system crashes, unauthorized access to sensitive information. |
| Phishing | Deceptive attempts to obtain sensitive details such as usernames, passwords, and credit card details by masquerading as a trustworthy entity in electronic communication. | Identity theft, financial loss, unauthorized access to systems. |
| Ransomware | Malware that encrypts files, demanding a ransom for their release. | Temporary or permanent loss of access to data, financial loss. |
| Man-in-the-Middle (MitM) Attacks | Eavesdropping on the communication between two parties who believe they are directly communicating with each other. | Interception of sensitive information, unauthorized transactions. |
| Distributed Denial of Service (DDoS) Attacks | Overwhelming a service with a flood of traffic, making it unavailable to its intended users. | Service disruption, loss of business during downtime. |
Each of these threats poses a significant risk to the continuity and security of operations. Understanding their mechanisms and impacts is crucial for developing effective strategies to mitigate these risks. By staying informed and proactive, organizations and individuals can better safeguard their digital assets against these evolving challenges.
The Impact of Data Loss on Businesses and Individuals
This section delves into the profound consequences that arise when critical digital assets are compromised or irretrievably lost. It explores how such incidents can disrupt both corporate operations and individual lives, emphasizing the need for robust strategies to mitigate these risks.
Economic Consequences: For enterprises, the financial repercussions of losing essential records or operational data can be staggering. Costs associated with downtime, recovery efforts, and potential legal liabilities can quickly escalate, leading to significant revenue losses and erosion of customer trust.
Operational Disruption: Data loss can paralyze business processes, halting production, and disrupting service delivery. This can lead to missed deadlines, contractual breaches, and a decline in operational efficiency, all of which can have long-term detrimental effects on a company’s market position.
Reputational Damage: In the digital age, news of data breaches or loss spreads rapidly. Such incidents can tarnish a company’s image, leading to a loss of consumer confidence and potentially damaging relationships with stakeholders. For individuals, exposure of sensitive details can lead to personal distress and vulnerability to identity theft or fraud.
Legal and Compliance Issues: Organizations operating in regulated industries face additional challenges. Data loss can lead to non-compliance with industry standards and legal requirements, resulting in hefty fines and legal actions. Maintaining data integrity and availability is crucial to avoid such pitfalls.
Personal Impact: On a personal level, losing digital assets such as family photos, important documents, or personal records can be emotionally devastating. The inability to recover these irreplaceable items can lead to a sense of loss and frustration, underscoring the personal value of data preservation.
Understanding these impacts is essential for developing effective strategies to safeguard digital assets. Whether for a business or an individual, the prevention of data loss is not just a technical issue but a critical aspect of overall risk management and digital resilience.
Choosing the Right Backup Solutions for Your Needs
In this section, we delve into the critical task of selecting appropriate strategies to ensure the safety and accessibility of essential records. The focus is on identifying methods that align with individual or organizational requirements, ensuring that all necessary precautions are taken to prevent potential mishaps.
When it comes to safeguarding vital documents, the choice of method is crucial. Various factors such as the volume of records, their sensitivity, and the frequency of updates should guide the selection process. Below is a table outlining different approaches and their suitability based on these factors:
| Backup Type | Suitability | Advantages | Disadvantages |
|---|---|---|---|
| Local Storage | Small to medium volumes of non-sensitive records | Quick access, no reliance on internet | Vulnerable to physical damage or theft |
| Cloud Services | Large volumes, sensitive data | Scalable, secure, accessible from anywhere | Requires stable internet connection, potential privacy concerns |
| Hybrid Solutions | Medium to large volumes, mixed sensitivity | Combines benefits of both local and cloud storage | Complex setup and management |
Each option has its merits and drawbacks, and the ideal choice depends on specific needs and circumstances. It is essential to consider the balance between convenience, security, and cost-effectiveness when making a decision.
Implementing a robust backup strategy involves not only selecting the right tools but also establishing protocols for regular updates and testing the integrity of stored data. This proactive approach ensures that in the event of an unforeseen incident, recovery is swift and complete, minimizing disruption and potential losses.
Best Practices for Implementing a Backup Plan

This section delves into effective strategies for establishing a robust system to preserve critical records. Ensuring the safety and accessibility of essential documents is paramount in today's digital age, where threats to digital assets are ever-present.
To effectively safeguard your crucial files, consider the following practices:
- Regular Scheduling: Establish a routine for backing up files. This should be done at least weekly, or more frequently for data that changes often.
- Multiple Storage Locations: Utilize at least two different storage mediums. This could include an external hard drive and a cloud service, ensuring that if one fails, the other can provide the necessary data.
- Automated Processes: Set up automatic backups to eliminate the risk of human error or forgetfulness. Many software solutions offer this feature, which can be customized to your specific needs.
- Encryption: Ensure that all backup data is encrypted. This adds an extra layer of security, protecting sensitive information from unauthorized access.
- Regular Verification: Periodically check the integrity of your backups. This involves testing the backups to ensure they can be restored successfully in case of data loss.
- Disaster Recovery Plan: Develop a comprehensive disaster recovery plan that includes steps to restore data from backups in various scenarios.
- Employee Training: Educate all team members about the backup procedures and their importance. This includes training on how to handle data and what to do in case of an emergency.
- Compliance with Regulations: Ensure that your backup practices comply with relevant data protection laws and regulations to avoid legal issues.
By adhering to these practices, you can significantly enhance the security and reliability of your data preservation efforts, mitigating the risks associated with data loss and ensuring business continuity.
The Future of Data Protection: Trends and Innovations
As we navigate through the digital age, the landscape of safeguarding sensitive details continues to evolve rapidly. This section delves into emerging methodologies and technological advancements that promise to redefine the strategies for preserving confidentiality and integrity in the realm of digital storage.
Advancements in Encryption Techniques
One of the pivotal trends in the forthcoming era of data safety is the refinement of encryption methodologies. Innovations such as quantum-resistant algorithms are being developed to fortify defenses against potential breaches, ensuring that even in the advent of quantum computing, sensitive details remain secure.
AI-Driven Threat Detection
Artificial intelligence is poised to play a crucial role in proactive threat detection. AI systems can analyze patterns and anomalies in real-time, enhancing the ability to identify and neutralize potential risks before they escalate into significant issues.
Cloud-Based Security Solutions
The shift towards cloud-based storage solutions is accompanied by advancements in cloud security. Enhanced access controls, multi-factor authentication, and continuous monitoring are becoming standard, offering robust protection against unauthorized access and data tampering.
Blockchain for Enhanced Transparency
Blockchain technology, known for its role in cryptocurrencies, is also finding applications in data protection. Its decentralized and immutable nature can be leveraged to create transparent and tamper-proof records, ensuring the integrity of stored information.
Customized Security Protocols
In the future, we can expect more personalized security protocols tailored to specific industries and even individual organizations. This customization will allow for more effective defense strategies that are aligned with the unique vulnerabilities and requirements of different sectors.
In conclusion, the future of safeguarding digital assets looks promising with a blend of technological advancements and strategic planning. As we continue to innovate, the focus remains on enhancing the resilience and adaptability of our security measures to protect against ever-evolving threats.
- 이전글ең ірі масштаб - ең ұсақ масштаб қайда қолданылады 24.09.26
- 다음글сиқырлы аниме мультфильмін қараңыз 24.09.26
댓글목록
등록된 댓글이 없습니다.

